Overview
IT Governance, Risk, and Compliance (GRC) is a strategy for managing an organizations overall governance, risk, and compliance in the cybersecurity and technology of a business and its key vendors.
- Governance - ensuring that activities support business goals.
- Risk - identifying, classifying, and addressing risk.
- Compliance - ensuring the business is meeting compliance with all legal and regulatory requirements.
Cybersecurity Frameworks
Blue Lightning Networks can help you implement your cybersecurity frameworks, whether you’re just starting out with CIS or NIST, or working on industry mandated frameworks such as HIPAA or PCI. We will map out an implementation plan based upon your industry requirements, current cybersecurity maturity, and risk tolerance and implement it on a risk prioritized basis.
The NIST Cybersecurity Framework:
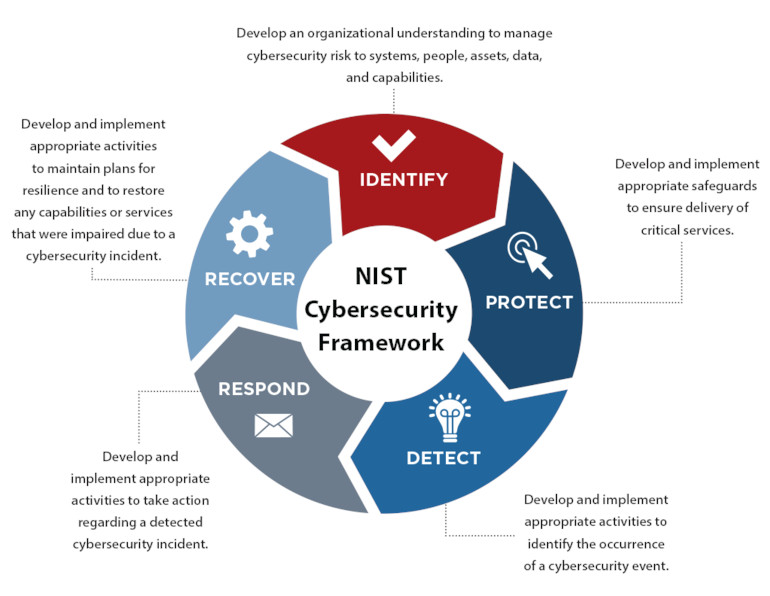
Risk Management
The heart of Blue Lightning Networks’ risk management platform is the continual monitoring of Open Source Intelligence (OSINT) sources for vulnerabilities, credential leaks, database leaks, etc. These sources are the same ones that hackers use to find their targets and their weaknesses. The platform can be utilized not only for self-monitoring, but also vendors and customers to analyze how their cybersecurity posture could affect you.
We continuously scan and compile the data we find into a simple, easily understandable report. Utilizing these data points, we can determine an overall Data Breach Index and Ransomware Susceptibility Index along with an annualized probable financial impact based upon the Open FAIR framework. Our high-level summary report groups these risks into an overall Cyber Rating (an A through F letter grade), and further into 20 letter-grade based categories under Safeguards, Privacy, Resiliency and Reputation. This report is an easy-to-understand visual guide for executives to quickly visualize and financially quantify their cyber risk.
We further analyze risks to a company by examining the internal vulnerabilities to determine what an attacker could exploit if they managed to breach the perimeter defenses. By deploying other tools behind your perimeter defenses, we can analyze potential internal risks and mitigate them.


